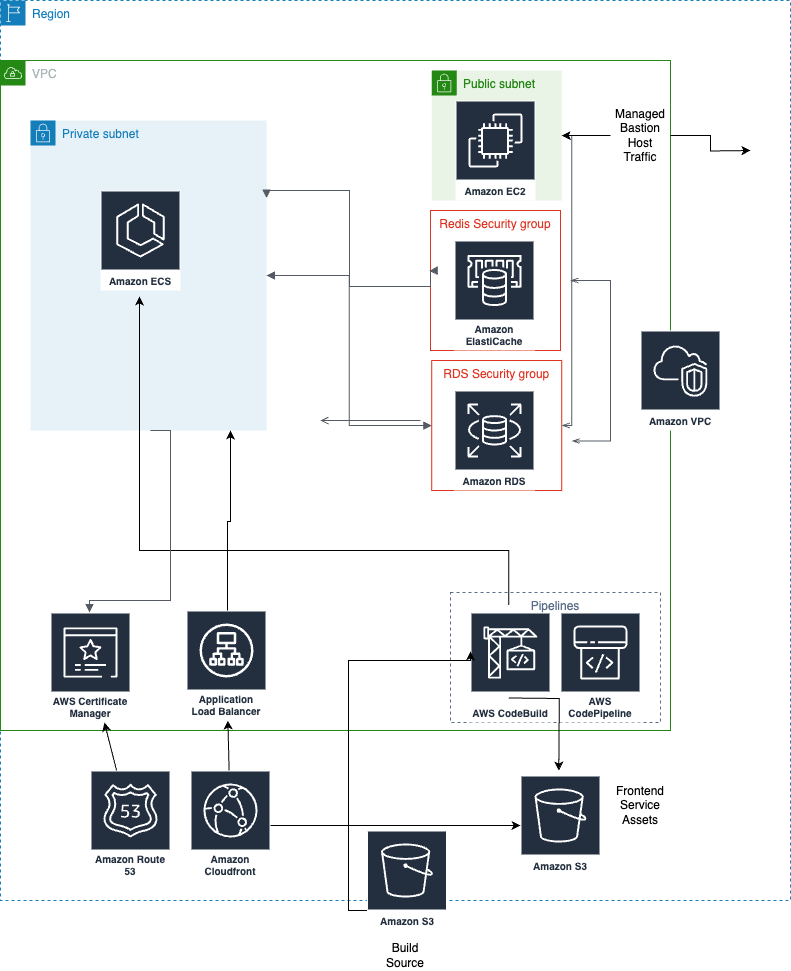
ECS Deep Dive
Resources Used
Networking
- A unique VPC is configured for each application. Multiple services in one application share a VPC.
- Each VPC has both a public and private subnet. ECS nodes are provisioned on the private subnet and use a NAT Gateway to route traffic to the rest of the network or to the internet.
- Route53 is used for DNS.
- By default, a subdomain of
cncsites.comis allocated to each application, and we point the NS records for that subdomain in our DNS provider at the NS records for the Route53 Zone in your account. - Custom domains (per-environment) are also supported, in which case you will designate NS records to Route53 directly from your own DNS provider.
- By default, a subdomain of
- ACM Certificates are used for secure HTTPS connections.
- ALB and ALB Listener are used for routing traffic to the backend services deployed on ECS. ALB Target Group is used to map to ECS services and manage health checks.
- CloudFront distributions are used for content delivery of frontend services hosted on S3. They are also used for traffic routing in backend services, but CDN functionality is not enabled by default for backend service types.
- If you have at least one backend service as well as a frontend service in your app, a Lambda@Edge is added to each environment's CloudFront distribution. This is because any non-200 response in CloudFront returns the distributions default error response, which means backend errors will be swallowed! Read more about this issue in Adam's blog post about the issue here.
{% callout type="note" title="NAT Gateway Costs" %} NAT gateway charges for all transit to the internet. Usage of the NAT gateway means that pulling docker impages into ECS tasks will incur transit costs (see AWS here). These can get expensive if frequent crons are used and especially if docker images are large.
Get in touch to talk about alternatives (we have some!) if this describes your use case {% /callout %}
Build & Deploy
- CodeBuild is used for building container images, running build steps such as asset compiling and testing the backend and frontend services, and is also used to manage ECS tasks spawned from the build to execute jobs like seeding or database migration.
- CodePipeline is used for continuous integration and deployment of the services.
Data Storage
Each AWS environment in Coherence gets a unique RDS instance. It also gets its own memorystore instance.
- S3 is used in 2 ways.
- Storing the enriched source code that coherence uploads to AWS each time you push to an environment (A shallow clone of your repo plus our generated configuration files).
- When you configure an object storage resource type in
coherence.ymlfor a service. In this case, we also add appropriate IAM permissions to the service's IAM role and inject the bucket name via environment variables. - Coherence configures AWS-managed KMS key for encryption by default. You can read more about S3 bucket encryption here.
- RDS DB Instance is used for the database of the application. RDS Proxy is used for supported Postgres versions in order to pool connections. Backups & high availability are not configured by default and the instance type is a
micro- changing these in the UI or with the CLI will not be treated as drift.- Coherence configures AWS-managed KMS key for encryption by default. You can view the encryption settings for your RDS instance following the AWS docs here.
- ElastiCache is used to provide managed redis instances to the application.
Container Orchestration
- ECS Fargate Cluster and Task Definitions are used for running the backend services, including scheduled tasks (cron) and private workers. Spot instances are automatically used for PR preview environments.
- App Autoscaling Policy and Target are used for automatic scaling of backend services on ECS.
Observability & Monitoring
- CloudWatch Log Group and Metric Alarm are used for monitoring and logging of the backend services. Metric alarms are used for ECS autoscaling rules.
Security & Configuration
Please note that Coherence enforces best practices around the usage of the root account in AWS. Read more about AWS best practice guidance here.
- Secrets Manager is used to store Environment Variables.
- IAM Role and Policy are used for providing permissions to the services. Distinct roles are provisioned with minimum permissions for different app components, such as building, deploying, and executing the application. You can customize these roles if needed.
- Workload Identities are used to assume app service accounts as needed without ever touching a key file.
- EC2 is used to provide a bastion host so that external connectivity to resources in the VPC is possible, from either your local network or Coherence's toolboxes.
Default Tags
For convenience and auditability, Coherence adds default tags to all cloud resources where applicable:
tags = {
Environment = "your-collection-name"
ManagedBy = "coherence"
Application = "your-application-name"
}
Diagram